Technology
Permacrisis: A Plan to Fix a Fractured World – review
In Permacrisis: A Plan to Fix a Fractured World, Gordon Brown, Mohamed El-Erian and Michael Spence put forward a strategy on growth, economic management and governance to prevent crises and shape a better society. Danny Dorling contends that the book’s suggested policy solutions for economic and social problems, stemming from a hypercapitalist ethos, would entrench rather than reduce inequalities.
Permacrisis: A Plan to Fix a Fractured World. Gordon Brown, Mohamed El-Erian and Michael Spence, with Reid Lidow. Simon & Schuster. 2023.
 Permacrisis is a remarkable book, but not for the reasons its authors might have hoped. It explains brilliantly why so much of our politics and economics is in such a terrible mess. The book argues that economic growth is progress, that we need this type of growth above all else to prosper, and that with just a minimal extra layer of regulation, such growth can spread the good life to the masses. Two quotations from Permacrisis, I believe, sum up both the core mantra of the three authors and what they think of as good growth and the good life. First, the mantra:
Permacrisis is a remarkable book, but not for the reasons its authors might have hoped. It explains brilliantly why so much of our politics and economics is in such a terrible mess. The book argues that economic growth is progress, that we need this type of growth above all else to prosper, and that with just a minimal extra layer of regulation, such growth can spread the good life to the masses. Two quotations from Permacrisis, I believe, sum up both the core mantra of the three authors and what they think of as good growth and the good life. First, the mantra:
”You see, growth is progress. Growth is what has given the world the tablet you’re reading this book on, the medicines by your bedside, the economic breakthroughs that have lifted billions out of poverty. The problem is how growth has been achieved […] the old unsustainable “profits over people” methods of the past have outstayed their welcome and today are not just failing individuals and our environment but national economies” (14).
[The authors] assume that the development of a tablet computer is due to economics rather than developments in universities and other state-funded bodies which created the micro-components that that enable a computer to be transmuted into tablet form.
The authors make a series of assumptions that help to explain why people like them think like they do. For example, in the above quotation, they assume that the development of a tablet computer is due to economics rather than developments in universities and other state-funded bodies which created the micro-components that that enable a computer to be transmuted into tablet form. Computers, and electricity before that, were not products of “the market” but technological inventions that have been marketised.
Perhaps they choose to assume their reader uses a tablet rather than a print copy because it is impossible to argue that the invention of the book, or typesetting or the printing press, was due to economic growth. This is because it happened long before the concept of economic growth existed, when a group of monks in Korea invented movable type in 1377. Instead, it was economic growth that got us to a state, in the Netherlands in the 1990s, where we were publishing more books than people could read by those purchasing them, peaking at over a thousand new titles a year per million potential readers (see image below). At this point, middle-class Dutch people stopped buying books just to display in their homes, and the publication of new titles plummeted (see Figure 12 below from the book Slowdown).
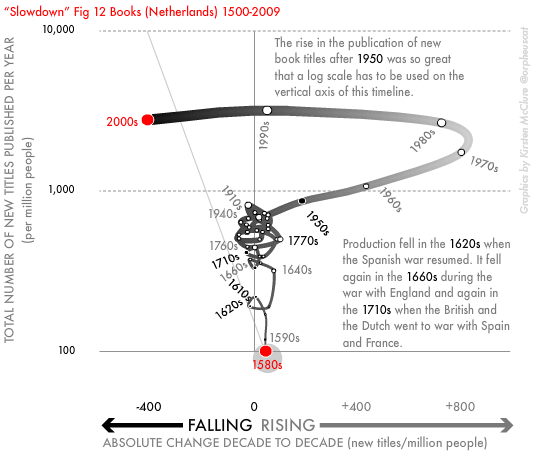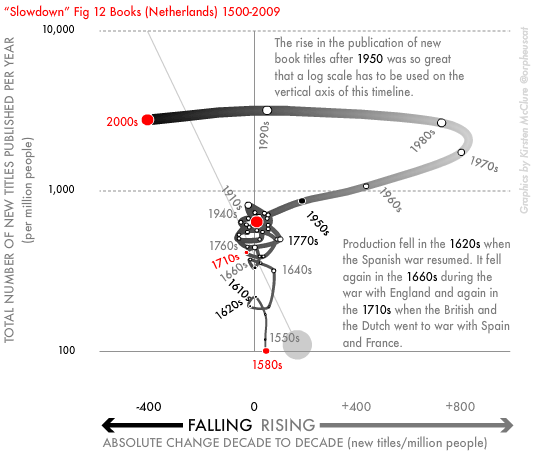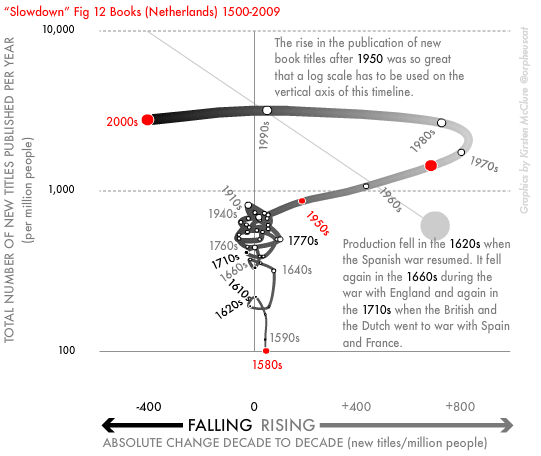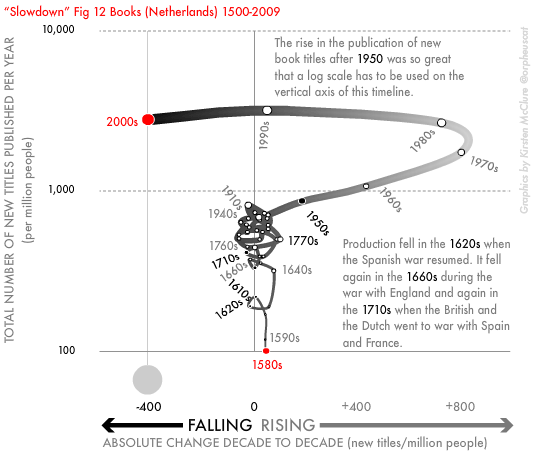
As the above example illustrates, economic growth can produce waste more than uplift and “progress” for the vast majority of people. Similarly, industrialisation reduced life expectancy not just in the mill towns of England, but across India. As I write global life expectancy hovers just above 70. In the US between 2020 and 2021, it dropped from 77 to 76.1, its lowest level since 1996. Most people in the world have far too little, a few have far too much. Social, medical, educational, housing, and cultural progress have all been made when the greediest aspects of market behaviour have been held in check, as the UK’s history of service provision demonstrates. Technological progress has depended on collaboration over profits. Those working in the US and UK produce very few innovations per head, as compared to people in the Nordic countries or Japan. But, the authors of this book appear utterly unaware of such arguments.
As with the tablet, the authors suggest that we have medicines because of economic growth rather than research and innovation; tellingly, the index to the book includes entries for “McKinsey” and “Pacific Investment Management Company (PIMCO)”, but none for “medicine” or “pharmaceuticals”.
As with the tablet, the authors suggest that we have medicines because of economic growth rather than research and innovation; tellingly, the index to the book includes entries for “McKinsey” and “Pacific Investment Management Company (PIMCO)”, but none for “medicine” or “pharmaceuticals”. This choice reveals what the book is actually about: the world of consultancy, international travel, and enormous amounts of money. McKinsey & Company is a global management consulting firm founded in 1926 by a University of Chicago professor (of accounting) that advises people with a lot of money how to acquire more. PIMCO, is an American investment firm that manages about two and a half trillion dollars of capital – to make more for people already rich. There is a pattern here.
Brown, El-Erian, and Spence suggest that, with a little more management by people like them, a little more of their kind of consulting, a little more of what they view as careful investment and better directing the trillions held by the world’s super rich, that we can somehow end the unsustainable “profits over people” behaviour of global economics.
The authors of this book believe that it was economic growth that “lifted billions out of poverty”. This view, along with the other core beliefs in Permacrisis, goes entirely unquestioned. Rather, Brown, El-Erian, and Spence suggest that, with a little more management by people like them, a little more of their kind of consulting, a little more of what they view as careful investment and better directing the trillions held by the world’s super rich, that we can somehow end the unsustainable “profits over people” behaviour of global economics. For them, the crisis is that they are not being listened to enough.
This brings us to how the book figures growth, and a second key quotation. In a long section celebrating the $1.50 Costco hot dog that entices shoppers through its doors, the authors explain their idea of economic growth and why they rate it so highly. Costco is a huge US chain of warehouses that started in 1976 as Price Club. It now has 125 million members, a number rising by around 6 million a year, and accelerating.
“The hotdog with the tantalising $1.50 price gets people in the door. And when they’re in the door, that’s when they see the knife set, back-yard patio set or the vacuum they can’t live without. And this business model has been a winner helping Costco reach a value in excess of $200 billion. Costco’s hotdog is a powerful and tasty reminder that growth isn’t always achieved by innovations developed in a Silicon Valley garage. Sometimes it’s as simple as keeping the price of a hotdog and soda steady – a decision that advances social goals by feeding those seeking an affordable snack, all while helping to power the growth of one of America’s largest companies. Costco’s chief financial officer was asked in late 2022 how long the $1.50 price would last. His response? Forever.” (30).
It is almost shocking to see such blatant endorsement of a particularly destructive form of economic growth, unplanned (at least as far as the consumer is concerned) instant gratification consumption, and such a warped view of social goals (to provide cheap hot dogs to the gullible).
Of the book’s authors – who were brought together by Jonny Geller of the global literary and talent agency, Curtis Brown (298) – one is Chief Advisor to “Allianz, the corporate parent of PIMCO, where he was CEO and co-CIO” (2) and husband of an executive director of Eco Oro Minerals Corp. Another was once UK Prime Minister and worked closely with Ed Balls, whose brother Andrew Balls has been for many decades a Chief Investment Officer of PIMCO (the other co-CIO). The third, who now lives in Milan, joined Oak Hill Capital in 1999 and was awarded a Nobel Prize in economics in 2001. They are what some economists view as masters of the universe: They believe their combined knowledge spans the breadth of global economic expertise: “While our personal and professional experience had natural touch points, like any good corporate merger the overlap and redundancy were minimal” (3). In fact, they are the crisis – and luckily, their beliefs are very far from permanent, sustainable or convincing, no matter how much they signal a sustainable ethos by adding the prefix ”‘eco-” before the ideas they put forward. In this book, they have encapsulated exactly what is wrong with the late twentieth-century hyper-capitalist worldview they champion that seeks to enrich the few and impoverish the rest of society.
Note: This review gives the views of the author, and not the position of the LSE Review of Books blog, or of the London School of Economics and Political Science. The LSE RB blog may receive a small commission if you choose to make a purchase through the above Amazon affiliate link. This is entirely independent of the coverage of the book on LSE Review of Books.
Main Image Credit: hachiware on Shutterstock.
Figure from Slowdown: Reproduced with the author’s permission.
Unlocking Pakistan’s 5G potential: A call to action
In March 1995, Pakistan’s Ministry of Information and Broadcasting took a bold step by granting a 15-year license to M/s Pay TV to establish a wireless TV network. The intention was clear: to harness the potential of wireless technology for the nation’s development. Years later, we find ourselves at a crossroads, with the promise of Continue reading »
Facebook Approved an Israeli Ad Calling for Assassination of Pro-Palestine Activist
A series of advertisements dehumanizing and calling for violence against Palestinians, intended to test Facebook’s content moderation standards, were all approved by the social network, according to materials shared with The Intercept.
The submitted ads, in both Hebrew and Arabic, included flagrant violations of policies for Facebook and its parent company Meta. Some contained violent content directly calling for the murder of Palestinian civilians, like ads demanding a “holocaust for the Palestinians” and to wipe out “Gazan women and children and the elderly.” Other posts, like those describing kids from Gaza as “future terrorists” and a reference to “Arab pigs,” contained dehumanizing language.
“The approval of these ads is just the latest in a series of Meta’s failures towards the Palestinian people.”
“The approval of these ads is just the latest in a series of Meta’s failures towards the Palestinian people,” Nadim Nashif, founder of the Palestinian social media research and advocacy group 7amleh, which submitted the test ads, told The Intercept. “Throughout this crisis, we have seen a continued pattern of Meta’s clear bias and discrimination against Palestinians.”
7amleh’s idea to test Facebook’s machine-learning censorship apparatus arose last month, when Nashif discovered an ad on his Facebook feed explicitly calling for the assassination of American activist Paul Larudee, a co-founder of the Free Gaza Movement. Facebook’s automatic translation of the text ad read: “It’s time to assassinate Paul Larudi [sic], the anti-Semitic and ‘human rights’ terrorist from the United States.” Nashif reported the ad to Facebook, and it was taken down.
The ad had been placed by Ad Kan, a right-wing Israeli group founded by former Israel Defense Force and intelligence officers to combat “anti-Israeli organizations” whose funding comes from purportedly antisemitic sources, according to its website. (Neither Larudee nor Ad Kan immediately responded to requests for comment.)
Calling for the assassination of a political activist is a violation of Facebook’s advertising rules. That the post sponsored by Ad Kan appeared on the platform indicates Facebook approved it despite those rules. The ad likely passed through filtering by Facebook’s automated process, based on machine-learning, that allows its global advertising business to operate at a rapid clip.
“Our ad review system is designed to review all ads before they go live,” according to a Facebook ad policy overview. As Meta’s human-based moderation, which historically relied almost entirely on outsourced contractor labor, has drawn greater scrutiny and criticism, the company has come to lean more heavily on automated text-scanning software to enforce its speech rules and censorship policies.
While these technologies allow the company to skirt the labor issues associated with human moderators, they also obscure how moderation decisions are made behind secret algorithms.
Last year, an external audit commissioned by Meta found that while the company was routinely using algorithmic censorship to delete Arabic posts, the company had no equivalent algorithm in place to detect “Hebrew hostile speech” like racist rhetoric and violent incitement. Following the audit, Meta claimed it had “launched a Hebrew ‘hostile speech’ classifier to help us proactively detect more violating Hebrew content.” Content, that is, like an ad espousing murder.
Incitement to Violence on Facebook
Amid the Israeli war on Palestinians in Gaza, Nashif was troubled enough by the explicit call in the ad to murder Larudee that he worried similar paid posts might contribute to violence against Palestinians.
Large-scale incitement to violence jumping from social media into the real world is not a mere hypothetical: In 2018, United Nations investigators found violently inflammatory Facebook posts played a “determining role” in Myanmar’s Rohingya genocide. (Last year, another group ran test ads inciting against Rohingya, a project along the same lines as 7amleh’s experiment; in that case, all the ads were also approved.)
The quick removal of the Larudee post didn’t explain how the ad was approved in the first place. In light of assurances from Facebook that safeguards were in place, Nashif and 7amleh, which formally partners with Meta on censorship and free expression issues, were puzzled.
“Meta has a track record of not doing enough to protect marginalized communities.”
Curious if the approval was a fluke, 7amleh created and submitted 19 ads, in both Hebrew and Arabic, with text deliberately, flagrantly violating company rules — a test for Meta and Facebook. 7amleh’s ads were designed to test the approval process and see whether Meta’s ability to automatically screen violent and racist incitement had gotten better, even with unambiguous examples of violent incitement.
“We knew from the example of what happened to the Rohingya in Myanmar that Meta has a track record of not doing enough to protect marginalized communities,” Nashif said, “and that their ads manager system was particularly vulnerable.”
Meta’s appears to have failed 7amleh’s test.
The company’s Community Standards rulebook — which ads are supposed to comply with to be approved — prohibit not just text advocating for violence, but also any dehumanizing statements against people based on their race, ethnicity, religion, or nationality. Despite this, confirmation emails shared with The Intercept show Facebook approved every single ad.
Though 7amleh told The Intercept the organization had no intention to actually run these ads and was going to pull them before they were scheduled to appear, it believes their approval demonstrates the social platform remains fundamentally myopic around non-English speech — languages used by a great majority of its over 4 billion users. (Meta retroactively rejected 7amleh’s Hebrew ads after The Intercept brought them to the company’s attention, but the Arabic versions remain approved within Facebook’s ad system.)
Facebook spokesperson Erin McPike confirmed the ads had been approved accidentally. “Despite our ongoing investments, we know that there will be examples of things we miss or we take down in error, as both machines and people make mistakes,” she said. “That’s why ads can be reviewed multiple times, including once they go live.”
Just days after its own experimental ads were approved, 7amleh discovered an Arabic ad run by a group calling itself “Migrate Now” calling on “Arabs in Judea and Sumaria” — the name Israelis, particularly settlers, use to refer to the occupied Palestinian West Bank — to relocate to Jordan.
According to Facebook documentation, automated, software-based screening is the “primary method” used to approve or deny ads. But it’s unclear if the “hostile speech” algorithms used to detect violent or racist posts are also used in the ad approval process. In its official response to last year’s audit, Facebook said its new Hebrew-language classifier would “significantly improve” its ability to handle “major spikes in violating content,” such as around flare-ups of conflict between Israel and Palestine. Based on 7amleh’s experiment, however, this classifier either doesn’t work very well or is for some reason not being used to screen advertisements. (McPike did not answer when asked if the approval of 7amleh’s ads reflected an underlying issue with the hostile speech classifier.)
Either way, according to Nashif, the fact that these ads were approved points to an overall problem: Meta claims it can effectively use machine learning to deter explicit incitement to violence, while it clearly cannot.
“We know that Meta’s Hebrew classifiers are not operating effectively, and we have not seen the company respond to almost any of our concerns,” Nashif said in his statement. “Due to this lack of action, we feel that Meta may hold at least partial responsibility for some of the harm and violence Palestinians are suffering on the ground.”
The approval of the Arabic versions of the ads come as a particular surprise following a recent report by the Wall Street Journal that Meta had lowered the level of certainty its algorithmic censorship system needed to remove Arabic posts — from 80 percent confidence that the post broke the rules, to just 25 percent. In other words, Meta was less sure that the Arabic posts it was suppressing or deleting actually contained policy violations.
Nashif said, “There have been sustained actions resulting in the silencing of Palestinian voices.”
The post Facebook Approved an Israeli Ad Calling for Assassination of Pro-Palestine Activist appeared first on The Intercept.
Online Atrocity Database Exposed Thousands of Vulnerable People in Congo
A joint project of Human Rights Watch and New York University to document human rights abuses in the Democratic Republic of the Congo has been taken offline after exposing the identities of thousands of vulnerable people, including survivors of mass killings and sexual assaults.
The Kivu Security Tracker is a “data-centric crisis map” of atrocities in eastern Congo that has been used by policymakers, academics, journalists, and activists to “better understand trends, causes of insecurity and serious violations of international human rights and humanitarian law,” according to the deactivated site. This includes massacres, murders, rapes, and violence against activists and medical personnel by state security forces and armed groups, the site said.
But the KST’s lax security protocols appear to have accidentally doxxed up to 8,000 people, including activists, sexual assault survivors, United Nations staff, Congolese government officials, local journalists, and victims of attacks, an Intercept analysis found. Hundreds of documents — including 165 spreadsheets — that were on a public server contained the names, locations, phone numbers, and organizational affiliations of those sources, as well as sensitive information about some 17,000 “security incidents,” such as mass killings, torture, and attacks on peaceful protesters.
The data was available via KST’s main website, and anyone with an internet connection could access it. The information appears to have been publicly available on the internet for more than four years.
Experts told The Intercept that a leak of this magnitude would constitute one of the most egregious instances ever of the online exposure of personal data from a vulnerable, conflict-affected population.
“This was a serious violation of research ethics and privacy by KST and its sponsoring organizations,” said Daniel Fahey, former coordinator of the United Nations Security Council’s Group of Experts on the Democratic Republic of the Congo, after he was told about the error. “KST’s failure to secure its data poses serious risks to every person and entity listed in the database. The database puts thousands of people and hundreds of organizations at risk of retaliatory violence, harassment, and reputational damage.”
“If you’re trying to protect people but you’re doing more harm than good, then you shouldn’t be doing the work in the first place.”
“If you’re an NGO working in conflict zones with high-risk individuals and you’re not managing their data right, you’re putting the very people that you are trying to protect at risk of death,” said Adrien Ogée, the chief operations officer at the CyberPeace Institute, which provides cybersecurity assistance and threat detection and analysis to humanitarian nongovernmental organizations. Speaking generally about lax security protocols, Ogée added, “If you’re trying to protect people but you’re doing more harm than good, then you shouldn’t be doing the work in the first place.”
The dangers extend to what the database refers to as Congolese “focal points” who conducted field interviews and gathered information for the KST. “The level of risk that local KST staff have been exposed to is hard to describe,” said a researcher close to the project who asked not to be identified because they feared professional reprisal. “It’s unbelievable that a serious human rights or conflict research organization could ever throw their staff in the lion’s den just like that. Militias wanting to take revenge, governments of repressive neighboring states, ill-tempered security services — the list of the dangers that this exposes them to is very long.”
The spreadsheets, along with the main KST website, were taken offline on October 28, after investigative journalist Robert Flummerfelt, one of the authors of this story, discovered the leak and informed Human Rights Watch and New York University’s Center on International Cooperation. HRW subsequently assembled what one source close to the project described as a “crisis team.”
Last week, HRW and NYU’s Congo Research Group, the entity within the Center on International Cooperation that maintains the KST website, issued a statement that announced the takedown and referred in vague terms to “a security vulnerability in its database,” adding, “Our organizations are reviewing the security and privacy of our data and website, including how we gather and store information and our research methodology.” The statement made no mention of publicly exposing the identities of sources who provided information on a confidential basis.
In an internal statement sent to HRW employees on November 9 and obtained by The Intercept, Sari Bashi, the organization’s program director, informed staff of “a security vulnerability with respect to the KST database which contains personal data, such as the names and phone numbers of sources who provided information to KST researchers and some details of the incidents they reported.” She added that HRW had “convened a team to manage this incident,” including senior leadership, security and communications staff, and the organization’s general counsel.
The internal statement also noted that one of HRW’s partners in managing the KST had “hired a third-party cyber security company to investigate the extent of the exposure of the confidential data and to help us to better understand the potential implications.”
“We are still discussing with our partner organizations the steps needed to fulfill our responsibilities to KST sources in the DRC whose personal information was compromised,” reads the statement, noting that HRW is working with staff in Congo to “understand, prepare for, and respond to any increase in security risks that may arise from this situation.” HRW directed staffers not to post on social media about the leak or publicly share any press stories about it due to “the very sensitive nature of the data and the possible security risks.”
The internal statement also said that “neither HRW, our partners, nor KST researchers in the DRC have received any information to suggest that anybody has been threatened or harmed as a result of this database vulnerability.”
The Intercept has not found any instances of individuals affected by the security failures, but it’s currently unknown if any of the thousands of people involved were harmed.
“We deeply regret the security vulnerability in the KST database and share concerns about the wider security implications,” Human Rights Watch’s chief communications officer, Mei Fong, told The Intercept. Fong said in an email that the organization is “treating the data vulnerability in the KST database, and concerns around research methodology on the KST project, with the utmost seriousness.” Fong added, “Human Rights Watch did not set up or manage the KST website. We are working with our partners to support an investigation to establish how many people — other than the limited number we are so far aware of — may have accessed the KST data, what risks this may pose to others, and next steps. The security and confidentiality of those affected is our primary concern.”

A peacekeeper of the United Nations Organization Stabilization Mission in the Democratic Republic of the Congo looks on in Sake, Democratic Republic of the Congo, on Nov. 6, 2023.
Photo: Glody Murhabzi/AFP via Getty Images
Bridgeway Foundation
Two sources associated with the KST told The Intercept that, internally, KST staff are blaming the security lapse on the Bridgeway Foundation, one of the donors that helped conceive and fund the KST and has publicly taken credit for being a “founding partner” of the project.
Bridgeway is the philanthropic wing of a Texas-based investment firm. Best known for its support for the “Kony 2012” campaign, the organization was involved in what a U.S. Army Special Operations Command’s historian called “intense activism and lobbying” that paved the way for U.S. military intervention in Central Africa. Those efforts by Bridgeway and others helped facilitate a failed $780 million U.S. military effort to hunt down Joseph Kony, the leader of a Ugandan armed group known as the Lord’s Resistance Army, or LRA.
More recently, the foundation was accused of partnering with Uganda’s security forces in an effort to drag the United States into “another dangerous quagmire” in Congo. “Why,” asked Helen Epstein in a 2021 investigation for The Nation, “is Bridgeway, a foundation that claims to be working to end crimes against humanity, involved with one of Africa’s most ruthless security agencies?”
One Congo expert said that Bridgeway has played the role of a “humanitarian privateer” for the U.S. government and employed tactics such as “private intelligence and military training.” As part of Bridgeway’s efforts to track down Kony, it helped create the LRA Crisis Tracker, a platform nearly identical to the KST that tracks attacks by the Ugandan militia. After taking an interest in armed groups in Congo, Bridgeway quietly pushed for the creation of a similar platform for Congo, partnering with NYU and HRW to launch the KST in 2017.
While NYU’s Congo Research Group oversaw the “collection and triangulation of data” for the KST, and HRW provided training and other support to KST researchers, the Bridgeway Foundation offered “technical and financial support,” according to a 2022 report by top foundation personnel, including Tara Candland, Bridgeway’s vice president of research and analysis, and Laren Poole, its chief operations officer. In a report published earlier this year, Poole and others wrote that the foundation had “no role in the incident tracking process.”
Several sources with ties to KST staff told The Intercept that Bridgeway was responsible for contracting the companies that designed the KST website and data collection system, including a tech company called Semantic AI. Semantic’s website mentions a partnership with Bridgeway to analyze violence in Congo, referring to their product as “intelligence software” that “allows Bridgeway and their partners to take action to protect the region.” The case study adds that the KST platform helps Bridgeway “track, analyze, and counter” armed groups in Congo.
Poole said that the KST had hired a cybersecurity firm to conduct a “comprehensive security assessment of the servers and hosting environment with the goal of better understanding the nature and extent of the exposure.” But it appears that answers to the most basic questions are not yet known. “We cannot currently determine when the security vulnerability occurred or how long the data was exposed,” Poole told The Intercept via email. “As recently as last year, an audit of the site was conducted that included assessing security threats, and this vulnerability was not identified.”
Like HRW, Bridgeway disclaimed direct responsibility for management of the KST’s website, attributing that work to two web development firms, Fifty and Fifty, which built and managed the KST from its inception until 2022, and Boldcode. That year, Poole said, “Boldcode was contracted to assume management and security responsibilities of the site.” But Poole said that “KST project leadership has had oversight over firms contracted for website development and maintenance since its inception.”
The Intercept did not receive a response to multiple messages sent to Fifty and Fifty. Boldcode did not immediately respond to a request for comment.
Warnings of Harm
Experts have been sounding the alarm about the dangers of humanitarian data leaks for years. “Critical incidents – such as breaches of platforms and networks, weaponisation of humanitarian data to aid attacks on vulnerable populations, and exploitation of humanitarian systems against responders and beneficiaries – may already be occurring and causing grievous harm without public accountability,” wrote a trio of researchers from the Signal Program on Human Security and Technology at the Harvard Humanitarian Initiative in 2017, the same year the KST was launched.
A 2022 analysis by the CyberPeace Institute identified 157 “cyber incidents” that affected the not-for-profit sector between July 2020 and June 2022. In at least 60 cases, personal data was exposed, and in at least 28, it was taken. “This type of sensitive personal information can be monetized or simply used to cause further harm,” the report says. “Such exploitation has a strong potential for re-victimization of individuals as well as the organizations themselves.”
In 2021, HRW itself criticized the United Nations Refugee Agency for having “improperly collected and shared personal information from ethnic Rohingya refugees.” In some cases, according to HRW, the agency had “failed to obtain refugees’ informed consent to share their data,” exposing refugees to further risk.
Earlier this year, HRW criticized the Egyptian government and a private British company, Academic Assessment, for leaving the personal information of children unprotected on the open web for at least eight months. “The exposure violates children’s privacy, exposes them to the risk of serious harm, and appears to violate the data protection laws in both Egypt and the United Kingdom,” reads the April report.
In that case, 72,000 records — including children’s names, birth dates, phone numbers, and photo identification — were left vulnerable. “By carelessly exposing children’s private information, the Egyptian government and Academic Assessment put children at risk of serious harm,” said Hye Jung Han, children’s rights and technology researcher and advocate at HRW at the time.
The threats posed by the release of the KST information are far greater than the Egyptian breach. For decades, Congo has been beset by armed violence, from wars involving the neighboring nations of Rwanda and Uganda to attacks by machete-wielding militias. More recently, in the country’s far east, millions have been killed, raped, or driven from their homes by more than 120 armed groups.
Almost all the individuals in the database, as well as their interviewers, appear to have confidentially provided sensitive information about armed groups, militias, or state security forces, all of which are implicated in grave human rights violations. Given the lawlessness and insecurity of eastern Congo, the most vulnerable individuals — members of local civil society organizations, activists, and residents living in conflict areas — are at risk of arrest, kidnapping, sexual assault, or death at the hands of these groups.
“For an organization working with people in a conflict zone, this is the most important type of data that they have, so it should be critically protected,” said CyberPeace Institute’s Ogée, who previously worked at European cybersecurity agencies and the World Economic Forum.
The KST’s sensitive files were hosted on an open “bucket”: a cloud storage server accessible to the open internet. Because the project posted monthly public reports on the same server that contained the sensitive information, the server’s URL was often produced in search engine results related to the project.
“The primary methodology in the humanitarian sector is ‘do no harm.’ If you’re not able to come into a conflict zone and do your work without creating any more harm, then you shouldn’t be doing it,” Ogée said. “The day that database is created and uploaded on that bucket, an NGO that is security-minded and thinks about ‘do no harm’ should have every process in place to make sure that this database never gets accessed from the outside.”
The leak exposed the identities of 6,000 to 8,000 individuals, according to The Intercept’s analysis. The dataset references thousands of sources labeled “civil society” and “inhabitants” of villages where violent incidents occurred, as well as hundreds of “youth” and “human rights defenders.” Congolese health professionals and teachers are cited hundreds of times, and there are multiple references to students, lawyers, psychologists, “women leaders,” magistrates, and Congolese civil society groups, including prominent activist organizations regularly targeted by the government.
“It’s really shocking,” said a humanitarian researcher with long experience conducting interviews with vulnerable people in African conflict zones. “The most important thing to me is the security of my sources. I would rather not document a massacre than endanger my sources. So to leave their information in the open is incredibly negligent. Someone needs to take responsibility.”

Residents of Bambo in Rutshuru territory in the Democratic Republic of the Congo flee rebel attacks on Oct. 26, 2023.
Photo: Alexis Huguet/AFP via Getty Images
Breach of Ethics
Since being contacted by The Intercept, the organizations involved have sought to distance themselves from the project’s lax security protocols.
In its internal statement to staff, HRW emphasized that it was not responsible for collecting information or supervising activities for KST, but was “involved in designing the research methodology, provided training, guidance and logistical support to KST researchers, and spot-checked some information.”
“HRW does not manage the KST website and did not set up, manage or maintain the database,” the internal statement said.
The Intercept spoke with multiple people exposed in the data leak who said they did not consent to any information being stored in a database. This was confirmed by four sources who worked closely with the KST, who said that gaining informed consent from people who were interviewed, including advising them that they were being interviewed for the KST, was not a part of the research methodology.
Sources close to the KST noted that its researchers didn’t identify who they were working for. The failure to obtain consent to collect personal information was likely an institutional oversight, they said.
“Obtaining informed consent is an undisputed core principle of research ethics,” the researcher who collaborated with the KST told The Intercept. “Not telling people who you work for and what happens to the information you provide to them amounts to lying. And that’s what has happened here at an unimaginable scale.”
In an email to NYU’s Center on International Cooperation and their Human Research Protections Program obtained by The Intercept, Fahey, the former coordinator of the Group of Experts on the Democratic Republic of the Congo, charged that KST staff “apparently failed to disclose that they were working for KST when soliciting information and did not tell sources how their information would be cataloged or used.”
In response, Sarah Cliffe, the executive director of NYU’s Center on International Cooperation, did not acknowledge Fahey’s concerns about informed consent, but noted that the institution takes “very seriously” concerns about the security of sources and KST staff exposed in the leak, according to an email seen by The Intercept. “We can assure you that we are taking immediate steps to investigate this and decide on the best course of action,” Cliffe wrote on November 1.
Fahey told The Intercept that NYU’s Human Research Protections Program did not respond to his questions about KST’s compliance with accepted academic standards and securing informed consent from Congolese informants. That NYU office includes the university’s institutional review board, or IRB, the body comprised of faculty and staff who review research protocols to ensure protection of human subjects and compliance with state and federal regulations as well as university policies.
NYU spokesperson John Beckman confirmed that while the KST’s researchers received training on security, research methodology, and research ethics, “including the importance of informed consent,” some of the people interviewed “were not informed that their personally identifiable information would be recorded in the database and were unaware that the information was to be used for the KST.”
Beckman added, “NYU is convening an investigative panel to review these human subject-related issues.”
Beckman also stated that the failure of Congolese “focal points” to provide informed consent tended to occur in situations that may have affected their own security. “Nevertheless, this raises troubling issues,” Beckman said, noting that all the partners involved in the KST “will be working together to review what happened, to identify what needs to be corrected going forward, and to determine how best to safeguard those involved in collecting and providing information about the incidents the KST is meant to track.”
Fong, of HRW, also acknowledged failures to provide informed consent in all instances. “We are aware that, while the KST researchers appropriately identified themselves as working for Congolese civil society organizations, some KST researchers did not in all cases identify themselves as working for KST, for security reasons,” she told The Intercept. “We are reviewing the research protocols and their implementation.”
“The partners have been working hard to try to address what happened and mitigate it,” Beckman told The Intercept, specifying that all involved were working to determine the safest method to inform those exposed in the leak.
Both NYU and HRW named their Congolese partner organization as being involved in some of the original errors and the institutional response.
The fallout from the exposure of the data may extend far beyond the breach of academic or NGO protocols. “Given the lack of security on KST’s website, it’s possible that intelligence agencies in Rwanda, Uganda, Burundi, DRC, and elsewhere have been accessing and mining this data for years,” Fahey said. “It is also possible that Congolese armed groups and national security forces have monitored who said what to KST staff.”
The post Online Atrocity Database Exposed Thousands of Vulnerable People in Congo appeared first on The Intercept.
From the Strip to the Border
How Israel profits from the arming of the U.S.-Mexico border.
LexisNexis Sold Powerful Spy Tools to U.S. Customs and Border Protection
The popular data broker LexisNexis began selling face recognition services and personal location data to U.S. Customs and Border Protection late last year, according to contract documents obtained through a Freedom of Information Act request.
According to the documents, obtained by the advocacy group Just Futures Law and shared with The Intercept, LexisNexis Risk Solutions began selling surveillance tools to the border enforcement agency in December 2022. The $15.9 million contract includes a broad menu of powerful tools for locating individuals throughout the United States using a vast array of personal data, much of it obtained and used without judicial oversight.
“This contract is mass surveillance in hyperdrive.”
Through LexisNexis, CBP investigators gained a convenient place to centralize, analyze, and search various databases containing enormous volumes of intimate personal information, both public and proprietary.
“This contract is mass surveillance in hyperdrive,” Julie Mao, an attorney and co-founder of Just Futures Law, told The Intercept. “It’s frightening that a rogue agency such as CBP has access to so many powerful technologies at the click of the button. Unfortunately, this is what LexisNexis appears now to be selling to thousands of police forces across the country. It’s now become a one-stop shop for accessing a range of invasive surveillance tools.”
A variety of CBP offices would make use of the surveillance tools, according to the documents. Among them is the U.S. Border Patrol, which would use LexisNexis to “help examine individuals and entities to determine their admissibility to the US. and their proclivity to violate U.S. laws and regulations.”
Among other tools, the contract shows LexisNexis is providing CBP with social media surveillance, access to jail booking data, face recognition and “geolocation analysis & geographic mapping” of cellphones. All this data can be queried in “large volume online batching,” allowing CBP investigators to target broad groups of people and discern “connections among individuals, incidents, activities, and locations,” handily visualized through Google Maps.
CBP declined to comment for this story, and LexisNexis did not respond to an inquiry. Despite the explicit reference to providing “LexisNexis Facial Recognition” in the contract, a fact sheet published by the company online says, “LexisNexis Risk Solutions does not provide the Department of Homeland Security” — CBP’s parent agency — “or US Immigration and Customs Enforcement with license plate images or facial recognition capabilities.”
The contract includes a variety of means for CBP to exploit the cellphones of those it targets. Accurint, a police and counterterror surveillance tool LexisNexis acquired in 2004, allows the agency to do analysis of real-time phone call records and phone geolocation through its “TraX” software.
While it’s unclear how exactly TraX pinpoints its targets, LexisNexis marketing materials cite “cellular providers live pings for geolocation tracking.” These materials also note that TraX incorporates both “call detail records obtained through legal process (i.e. search warrant or court order) and third-party device geolocation information.” A 2023 LexisNexis promotional brochure says, “The LexisNexis Risk Solutions Geolocation Investigative Team offers geolocation analysis and investigative case assistance to law enforcement and public safety customers.”
Any CBP use of geolocational data is controversial, given the agency’s recent history. Prior reporting found that, rather than request phone location data through a search warrant, CBP simply purchased such data from unregulated brokers — a practice that critics say allows the government to sidestep Fourth Amendment protections against police searches.
According to a September report by 404 Media, CBP recently told Sen. Ron Wyden, D-Ore., it “will not be utilizing Commercial Telemetry Data (CTD) after the conclusion of FY23 (September 30, 2023),” using a technical term for such commercially purchased location information.
The agency, however, also told Wyden that it could renew its use of commercial location data if there were “a critical mission need” in the future. It’s unclear if this contract provided commercial location data to CBP, or if it was affected by the agency’s commitment to Wyden. (LexisNexis did not respond to a question about whether it provides or provided the type of phone location data that CBP had sworn off.)
The contract also shows how LexisNexis operates as a reseller for surveillance tools created by other vendors. Its social media surveillance is “powered by” Babel X, a controversial firm that CBP and the FBI have previously used.
According to a May 2023 report by Motherboard, Babel X allows users to input one piece of information about a surveillance target, like a Social Security number, and receive large amounts of collated information back. The returned data can include “social media posts, linked IP address, employment history, and unique advertising identifiers associated with their mobile phone. The monitoring can apply to U.S. persons, including citizens and permanent residents, as well as refugees and asylum seekers.”
While LexisNexis is known to provide similar data services to U.S. Immigration and Customs Enforcement, another division of the Department of Homeland Security, details of its surveillance work with CBP were not previously known. Though both agencies enforce immigration law, CBP typically focuses on enforcement along the border, while ICE detains and deports migrants inland.
In recent years, CBP has drawn harsh criticism from civil libertarians and human rights advocates for its activities both at and far from the U.S.-Mexico border. In 2020, CBP was found to have flown a Predator surveillance drone over Minneapolis protests after the murder of George Floyd; two months later, CBP agents in unmarked vehicles seized racial justice protesters off the streets of Portland, Oregon — an act the American Civil Liberties Union condemned as a “blatant demonstration of unconstitutional authoritarianism.”
Just Futures Law is currently suing LexisNexis over claims it illegally obtains and sells personal data.
The post LexisNexis Sold Powerful Spy Tools to U.S. Customs and Border Protection appeared first on The Intercept.
Google Activists Circulated Internal Petition on Israel Ties. Only the Muslim Got a Call from HR.
A Google employee protesting the tech giant’s business with the Israeli government was questioned by Google’s human resources department over allegations that he endorsed terrorism, The Intercept has learned. The employee said he was the only Muslim and Middle Easterner who circulated the letter and also the only one who was confronted by HR about it.
The employee was objecting to Project Nimbus, Google’s controversial $1.2 billion contract with the Israeli government and its military to provide state-of-the-art cloud computing and machine learning tools.
Since its announcement two years ago, Project Nimbus has drawn widespread criticism both inside and outside Google, spurring employee-led protests and warnings from human rights groups and surveillance experts that it could bolster state repression of Palestinians.
Mohammad Khatami, a Google software engineer, sent an email to two internal listservs on October 18 saying Project Nimbus was implicated in human rights abuses against Palestinians — abuses that fit a 75-year pattern that had brought the conflict to the October 7 Hamas massacre of some 1,200 Israelis, mostly civilians. The letter, distributed internally by anti-Nimbus Google workers through company email lists, went on to say that Google could become “complicit in what history will remember as a genocide.”
“Strangely enough, I was the only one of us who was sent to HR over people saying I was supporting terrorism or justifying terrorism.”
Twelve days later, Google HR told Khatami they were scheduling a meeting with him, during which he says he was questioned about whether the letter was “justifying the terrorism on October 7th.”
In an interview, Khatami told The Intercept he was not only disturbed by what he considers an attempt by Google to stifle dissent on Nimbus, but also believes he was left feeling singled out because of his religion and ethnicity. The letter was drafted and internally circulated by a group of anti-Nimbus Google employees, but none of them other than Khatami were called by HR, according to Khatami and Josh Marxen, another anti-Nimbus organizer at Google who helped spread the letter. Though he declined to comment on the outcome of the HR meeting, Khatami said it left him shaken.
“It was very emotionally taxing,” Khatami said. “I was crying by the end of it.”
“I’m the only Muslim or Middle Eastern organizer who sent out that email,” he told The Intercept. “Strangely enough, I was the only one of us who was sent to HR over people saying I was supporting terrorism or justifying terrorism.”
The Intercept reviewed a virtually identical email sent by Marxen, also on October 18. Though there are a few small changes — Marxen’s email refers to “a seige [sic] upon all of Gaza” whereas Khamati’s cites “the complete destitution of Gaza” — both contain verbatim language connecting the October 7 attack to Israel’s past treatment of Palestinians.
Google spokesperson Courtenay Mencini told The Intercept, “We follow up on every concern raised, and in this case, dozens of employees reported this individual’s email – not the sharing of the petition itself – for including language that did not follow our workplace policies.” Mencini declined to say which workplace policies Khatami’s email allegedly violated, whether other organizers had gotten HR calls, or if any other company personnel had been approached by Employee Relations for comments made about the war.
The incident comes just one year after former Google employee Ariel Koren said the company attempted to force her to relocate to Brazil in retaliation for her early anti-Nimbus organizing. Koren later quit in protest and remains active in advocating against the contract. Project Nimbus, despite the dissent, remains in place, in part because of contractual terms put in place by Israel forbidding Google from cutting off service in response to political pressure or boycott campaigns.
Dark Clouds Over Nimbus
Dissent at Google is neither rare nor ineffective. Employee opposition to controversial military contracts has previously pushed the company to drop plans to help with the Pentagon’s drone warfare program and a planned Chinese version of Google Search that would filter out results unwanted by the Chinese government. Nimbus, however, has managed to survive.
In the wake of the October 7 Hamas attacks against Israel and resulting Israeli counteroffensive, now in its second month of airstrikes and a more recent ground invasion, Project Nimbus is again a flashpoint within the company.
With the rank and file disturbed by the company’s role as a defense contractor, Google has attempted to downplay the military nature of the contract.
Mencini, the Google spokesperson, said that anti-Nimbus organizers were “misrepresenting” the contract’s military role.
“This is part of a longstanding campaign by a group of organizations and people who largely don’t work at Google,” Mencini said. “We have been very clear that the Nimbus contract is for workloads running on our commercial platform by Israeli government ministries such as finance, healthcare, transportation, and education. Our work is not directed at highly sensitive or classified military workloads relevant to weapons or intelligence services.”
Nimbus training documents published by The Intercept last year, however, show the company was pitching its use for the Ministry of Defense. Moreover, the Israeli government itself is open about the military applications of Project Nimbus: A 2023 press release by the Israeli Ministry of Finance specifically names the Israel Defense Forces as a beneficiary, while an overview written by the country’s National Digital Agency describes the contract as “a comprehensive and in-depth solution to the provision of public cloud services to the Government, the defense establishment and other public organizations.”
“If we do not speak out now, we are complicit in what history will remember as a genocide.”
Against this backdrop, Khatami, in coordination with others in the worker-led anti-Nimbus campaign, sent his October 18 note to internal Arab and Middle Eastern affinity groups laying out their argument against the project and asking like-minded colleagues to sign an employee petition.
“Through Project Nimbus, Google is complicit in the mass surveillance and other human rights abuses which Palestinians have been subject to daily for the past 75 years, and which is the root cause of the violence initiated on October 7th,” the letter said. “If we do not speak out now, we are complicit in what history will remember as a genocide.”
On October 30, Khatami received an email from Google’s Employee Relations division informing him that he would soon be questioned by company representatives regarding “a concern about your conduct that has been brought to our attention.”
According to Khatami, in the ensuing phone call, Google HR pressed him about the portion of his email that made a historical connection between the October 7 Hamas attack and the 75 years of Israeli rights abuses that preceded it, claiming some of his co-workers believed he was endorsing violence. Khatami recalled being asked, “Can you see how people are thinking you’re justifying the terrorism on October 7th?”
Khatami said he and his fellow anti-Nimbus organizers were in no way endorsing the violence against Israeli civilians — just as they now oppose the deaths of more than 10,000 Palestinians, according to the latest figures from Gaza’s Ministry of Health. Rather, the Google employees wanted to provide sociopolitical context for Project Nimbus, part of a broader employee-led effort of “demilitarizing our company that was never meant to be militarized.” To point out the relevant background leading to the October 7 attack, he said, is not to approve it.
“We wrote that the root cause of the violence is the occupation,” Khatami explained. “Analysis is not justification.”
Double Standard
Khatami also objects to what he said is a double standard within Google about what speech about the war is tolerated, a source of ongoing turmoil at the company. The day after his original email, a Google employee responded angrily to the email chain: “Accusing Israel of genocide and Google of being complicit is a grave accusation!” This employee, who works at the company’s cloud computing division, itself at the core of Project Nimbus, continued:
To break it down for you, project nimbus contributes to Israel’s security. Therefore, any calls to drop it are meant to weaken Israel’s security. If Israel’s security is weak, then the prospect of more terrorist attacks, like the one we saw on October 7, is high. Terrorist attacks will result in casualties that will affect YOUR Israeli colleagues and their family. Attacks will be retaliated by Israel which will result in casualties that will affect your Palestinian colleagues and their family (because they are used as shields by the terrorists)…bottom line, a secured Israel means less lives lost! Therefore if you have the good intention to preserve human lives then you MUST support project Nimbus!
While Khatami disagrees strongly with the overall argument in the response email, he objected in particular to the co-worker’s claim that Israel is killing Palestinians “because they are used as shields by the terrorists” — a justification of violence far more explicit than the one he was accused of, he said. Khatami questioned whether widespread references to the inviolability of Israeli self-defense by Google employees have provoked treatment from HR similar to what he received after his email about Nimbus.
Internal employee communications viewed by The Intercept show tensions within Google over the Israeli–Palestinian conflict aren’t limited to debates over Project Nimbus. A screenshots viewed by The Intercept shows an Israeli Google employee repeatedly asking Middle Eastern colleagues if they support Hamas, while another shows a Google engineer suggesting Palestinians worried about the welfare of their children should simply stop having kids. Another lamented “friends and family [who] are slaughtered by the Gaza-grown group of bloodthirsty animals.”
According to a recent New York Times report, which found “at least one” instance of “overtly antisemitic” content posted through internal Google channels, “one worker had been fired after writing in an internal company message board that Israelis living near Gaza ‘deserved to be impacted.’”
Another screenshot reviewed by The Intercept, taken from an email group for Israeli Google staff, shows employees discussing a post by a colleague criticizing the Israeli occupation and encouraging donations to a Gaza relief fund.
“During this time we all need to stay strong as a nation and united,” one Google employee replied in the email group. “As if we are not going through enough suffering, we will unfortunately see many emails, comments either internally or on social media that are pro Hamas and clearly anti semitic. report immediately!” Another added: “People like that make me sick. But she is a lost cause.” A third chimed in to say they had internally reported the colleague soliciting donations. A separate post soliciting donations for the same Gaza relief fund was downvoted 139 times on an internal message board, according to another screenshot, while a post stating only “Killing civilians is indefensible” received 51 downvotes.
While Khatami says he was unnerved and disheartened by the HR grilling, he’s still committed to organizing against Project Nimbus.
“It definitely emotionally affected me, it definitely made me significantly more fearful or organizing in this space,” he said. “But I think knowing that people are dying right now and slaughtered in a genocide that’s aided and abetted by my company, remembering that makes the fear go away.”
The post Google Activists Circulated Internal Petition on Israel Ties. Only the Muslim Got a Call from HR. appeared first on The Intercept.
Philosopher Chosen to Lead Center on “Computation and Just Communities”
Dartmouth University earlier this fall launched its Susan and James Wright Center for the Study of Computation and Just Communities, and named philosophy professor Susan Brison as its inaugural director.

The interdisciplinary center focuses on
understanding the role of computation in informing essential questions about good governance, human rights, and the relationship between governments and the governed. Using tools such as computer simulations, machine learning, artificial intelligence, and complex statistical analysis, initiatives supported by the center will explore a broad range of topics, many of which expose the double-edged sword of computational advances in the public and governmental sphere. The topics will include the dynamics of surveillance and safety, the protection of free speech in a time of widespread of misinformation, and the dangers—as well as the artistic possibilities—of image manipulation and creation.
The center will host workshops and lectures, and fund research.
More information here.
The post Philosopher Chosen to Lead Center on “Computation and Just Communities” first appeared on Daily Nous.
Two Journeys with the Putney Punt
On display in the City of Canada Bay Museum is a model of the car ferry that crosses the Parramatta River between Mortlake and Putney. Although officially known as the Mortlake Ferry, it is more familiarly known as the Putney Punt. The service has carried traffic across the stretch of river between Mortlake, on Wangal land to the south, and Putney, on Wallumedegal land to the north, since 1928.
Among the varied collection of the museum, the model of the ferry can be found in between a glass case with a wedding dress inside of it, and another with a model of one of the gasometer tanks that used to dominate the Mortlake peninsula when it was a gasworks. The model of the ferry is long and narrow, bracketed by a wharf on either end, with a track between, on which the ferry moves once you press the green button on the side of the case. It’s meticulously made and specific in its details, the little round lifebuoys labelled with DMR (Department of Main Roads, which became RTA, now RMS) and a box of life jackets, as well as some very 70s-looking Matchbox cars parked on the ferry itself, and little reflective road signs at each wharf showing the timetable.
I press the button and the motor starts up. The ferry begins to move across the painted river, slowly advancing towards the Putney side. The motor hums as it makes it slow way, before stopping with a click once it reaches its destination. At first I had thought the model had been built specifically for the museum, but in fact it had been made by the DMR for display at the wharf, alongside where the actual ferry plies its route across the river. It had been housed inside the waiting room on the Mortlake side as a curiosity, demonstrating the ferry’s mechanism – how it operates by two cables, one which pulls, and one which guides, conveying it from one side to the other.
 The model by the wharf, in 1988, photo: City of Canada Bay Local Studies Collection
The model by the wharf, in 1988, photo: City of Canada Bay Local Studies Collection
When the model was displayed at the wharf it was thought the ferry would be decommissioned. By the late 1980s, when plans to remove it were afoot, the punt was regarded as a relic of Mortlake’s industrial past, in operation as it was for the convenience of the employees at the gasworks, who would come across from the north side to go to work.
 The Putney Punt in 1988, with gasometer in the background, photo: City of Canada Bay Local Studies Collection
The Putney Punt in 1988, with gasometer in the background, photo: City of Canada Bay Local Studies Collection
It was the last of the car ferries in metropolitan Sydney: others, at Ryde, Tom Ugly’s Point, and The Spit, had all long-before been replaced by bridges. Recognising the Putney Punt’s significance, there were protests about its removal and about the proposed $1 toll if it did remain. The National Trust listed the ferry and although the gasworks was redeveloped into the residential suburb of Breakfast Point, the ferry has continued to operate. The model did not fare quite so well at the time, falling into disrepair, before being retired to the museum. Here, it was restored back to working order by the local Men’s Shed.
Mortlake is only a slip of a suburb now, a mixture of houses, apartments, and a few remaining small factories along the road that leads to the wharf. After the road passes by the factories and apartment buildings, all of a sudden there is a sharp turn to the right. Then there’s the unusual sight of the road extending all the way to the edge of the riverbank, beyond the boom gates where cars wait to cross.
It is a quiet day, a public holiday, and there are no other cars waiting behind the stop sign. I’m the only one, and I get out to step closer to the gate, to look across at the ferry, which is over on the Putney side, with a few cars slowly driving onto it. To either side of the wharf the headlands curve in and out around the water, which is a pale silvery blue on this overcast day. In the distance, over in the east, the city skyline looks smaller than I expect it to, its high-rise buildings more spread out from this vantage point.
The ferry is making its way across now, painted cream and green, familiar from the model, slowly advancing and enlarging as it draws closer. It reaches the wharf and stops with a thunk as the lip of the ferry aligns with the road, and the cars drive off. Then it’s my turn. The ferry master beckons and I drive forwards, stopping in the front middle of the three lanes. It doesn’t feel unusual until the ferry gets going, away from the wharf and out across the river, and I have the sensation of the car moving while being stationery, a more fluid, buoyant motion than driving.
It’s fun to traverse the river this way, a change of perspective, suddenly afloat, in what was described in an article about the punt from 1954, as ‘a moment of leisure’, and ‘four minutes of enforced inaction, as refreshing as a summer shower’. At that time, in the 1950s, with industry in full operation, the river was polluted and its beaches choked with piles of rusting debris, and the water, so the article describes it, was a ‘drab maroon with the noisome effluent from the gasworks’. It has come a long way towards repair since that time.
For all its shift in perspective it’s only a quick journey, and after a couple more minutes the punt comes in at an angle to the Putney wharf, working with the resistance of the tide. It swings into place at the last minute, pulled in by the thick metal cables. The boom gate opens and the ferry master beckons me to drive forward, and suddenly I’m on the north side, among the suburban streets, driving past houses with bright purple tibouchina flowers in their gardens, back on solid ground.
A Telex from Bankstown
To the north side of Bankstown station the rows of shops are under a cloak of rain, with a grey sky above. It has been a few years since I’ve last been over this way, and through the gloom of the rain I look for some of the details I remember: a ghost sign for curtains and home linens, ‘Optical House’, and the inscrutable facade of the Telstra Museum. As long as I’ve known it to be there I’ve wondered what is inside, the building’s plain appearance only heightening its mystery.
This time, I go up to the entrance, and seeing that it’s a Wednesday and the sign indicates it is open, I press the doorbell. Nothing happens for a little while, but I wait. There are few clues to it being open from the street, the windows have frosted glass and heavy grilles, which make it difficult even to see if the lights are on inside. But after a minute or so the door opens, and a museum guide welcomes me in.
Never have I been in a room with so many telephones. Immediately it is clear this is a comprehensive and loved collection of telecommunications objects, arranged by type and category, in aisles signposted ‘telephone exchanges, public telephones’, or ‘morse code, teleprinters’. Soon I’m examining a row of public telephones, pointing out to the guide the ones I remember: ah, the gold phone, phone of my teenage years.
Telephone technology has undergone constant change since its inception in the mid-nineteenth century, progressing from contraptions of wires and bells and plugs, through a series of advancements towards digital systems, a narrative documented here in the Telstra Museum through objects and ephemera.
My guide, like many of the museum’s volunteers, had worked for PMG, the Postmaster General’s Department, which handled post and telecommunications before the services were split in the 1970s, into Australia Post and Telecom. He shows me how the switchboard exchange mechanisms worked and we take up a bakelite phone each to role play a phone call as he guides me through the operation of the pyramid switchboard. Switchboard operators were generally women, who were thought to be more patient and polite for a job which required continual conversations with callers: my fumbling attempts were once actions conducted with great speed and precision.
We examine exchange equipment, morse code machines, teleprinters, and the Muirhead-Jarvis Picture Transmitter, which relayed news photographs by telegram, in a machine housed in a cabinet something like a piano, that prefigured the fax machine and the photocopier. One aisle is dedicated to domestic telephones, including a rotary dial phone in gold, which is, I see when I go up close, ‘the one millionth telephone manufactured by STC’.
Other phones have tapestry covers, or are wall mounted and in a range of colours (Powder Blue, Maize Yellow, Cinnamon). A photocopied illustration shows the Dolly Vardin cover that was fashionable in the early 1900s with those who found the sight of the telephone unattractive, a doll with a long lacy skirt, tall enough to cover over the telephone underneath.
These phones and communication devices were once regarded as new, then became everyday items, then were outmoded, to finally became museum pieces. In one section are the first mobile phones and car phones, big clunky bricks that cost many thousands of dollars in the 80s and 90s. I’m drawn to an earlier innovation, an alternative 1960s design for landline phones. The Ericofon, the guide tells me, came to be popular for use in airport operations, but they weren’t so popular in homes, because if you needed to put the phone down mid-call you had to remember to put it on its side, or else you’d hang up on the caller.
In the last row of the museum, beside a radio studio and ‘television operations centre’, is George the Speaking Clock. You have George? I ask, with a growing sense of excitement. In 2018 I wrote an essay for the Powerhouse Museum book Time and Memory, and researched 20th century methods of time keeping and recording, of which George was one. I draw closer to the machine which had once announced the current time to callers, from a series of three glass discs on which was recorded the voice of a radio announcer named Gordon (not George) Gow. One disc held the hours, one the minutes, and another the seconds, and the machine selected the correct combination of numbers according to the current time.
In the essay, I had described a call to George: “Upon calling B074, callers heard Gow’s voice cycling through the 4320 announcements that made up one day’s worth of time. At the hour, when the time announcement was followed by ‘precisely’, his voice seemed to relish the crispness of the word — indeed, the speaking clock was advertised as being accurate to within one-hundredth of a second.”
In his heyday, George attracted many thousands of calls a day, but here, in the Telstra Museum, he reads the time just for me, as the guide wakes him up for a solo performance.
Telegram stationery, pneumatic tubes, post office memorabilia, Beepa the Owl (the 1980s Telecom mascot), Telecom-patterned tableware… there was seemingly no limit to the technical and cultural ephemera of communications, and I vowed to return, another day, for a morse code demonstration and further investigation of the collection.
Like George and the Goldphone public phone, the crockery was familiar to me too. Many years ago I’d bought a Telecom teacup from an op shop, and so after navigating the wet, potholed streets back home, I settled down to warm up with a cup of tea in my own piece of telecommunications history.
_
With thanks to Jeff and Bob for their museum tour and demonstrations.















